The most complicated part of the implementation of ISO 27001 is risk management. It is also the most important step at the beginning of any information security project as it lays the foundation of information security in any company.
ISO 27001 risk assessment template using in project management documents planning & creating new project plan. Check out ISO project Documentation templates.
There are two basic elements of risk management:
- R Assessment also called risk analysis
- Risk treatment
A Risk Assessment Template for ISO 27001 is a valuable tool used to identify, evaluate, and manage risks associated with information security within an organization. ISO 27001 is an internationally recognized standard that provides a framework for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS).
The Risk Assessment Template is designed to help organizations systematically assess potential risks to their information assets and determine appropriate controls to mitigate those risks. The template typically includes various sections that guide users through the risk assessment process. These sections may include identifying assets, assessing threats and vulnerabilities, determining the likelihood and impact of risks, and recommending controls.
Risk Assessment/Analysis
The process during which an organization identifies risks to its information security, and their impact on the organization, is call risk assessment. In other words, the organization should recognize all the problems that can occur with their information, the likeliness of their occurrence, and their consequences.
ISO 27001 is one of the most popular standards for information security throughout the world. The companies that have achieve compliance with this standard can prove that they are serious about how they handle and use the information.
The template begins by identifying the information assets that need protection, such as sensitive customer data, intellectual property, or critical infrastructure. It then prompts the user to assess potential threats and vulnerabilities that could exploit these assets. This step involves analyzing internal and external threats, as well as identifying any weaknesses in the organization’s security measures.

ISO 27001 also gives confidence to the client that the company they are dealing with is managing the integrity, confidentiality, and availability of the provided information.
ISO 27001 risk assessment Template (Key Features)
Risk assessment can be a difficult and complex process but it can be simplified by dividing it into the following steps:
Define the methodology for risk assessment
This is the first step of risk management in ISO 27001. All the parts of the organization must perform the risk assessment in the same way, thus, some rules must be defined for performing the risk management.
It should be determined whether a qualitative or quantitative risk assessment needs to be done, what scales will be used for qualitative assessment, what the acceptable level of risk can be, etc.
Many organizations make the risk assessment process very difficult by defining the wrong ISO 27001 risk assessment methodology or by not defining the methodology at all.
According to Clause 6.1.2 of ISO 27001, it is necessary to document the entire risk assessment process and the document is called risk assessment methodology. The following are the requirements of ISO 27001 risk assessment methodology: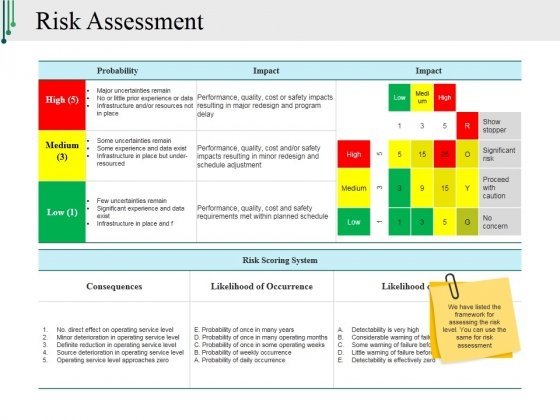
Using Risk Assessment Template for ISO 27001, you can easily create methodology.
- Describe how to identify the risks that could cause the loss of integrity, confidentiality, or availability of your information. This can be done by identifying the threats, assets, and vulnerabilities.
- Describe how to identify the owners of the risk. Risk owners are the persons interested in the risk and positioned at such high levels in the organization that they can do anything about the risk.
- criteria for assessing the likelihood of the risks and their consequences.
- how the risk will be calculated?
- Describe the criteria according to which the risks will be accepted. As every risk cannot be eliminated, the level of residual risk that the company is willing to leave unaddressed should be decided.
So, these five key elements are needed for an effective risk assessment. Anything less will not be enough and anything more than this is not required. Thus, by defining these elements, the organization can prevent the complication of the process.
Related Template: ISO Document Control Template
Put together a list of the information assets
Assets include electronic files, intellectual property, hard copies of data, removable media, mobile devices, etc. ISO 27001 allows organizations to take an asset-based approach because you can work using an existing list of information assets.
Identify risks and vulnerabilities
Once a list of all the information asses has been compiled, risks and vulnerabilities can be determined. Identifying the risks that can impact the integrity, confidentiality, or availability of information is one of the most important as well as time-consuming elements of the risk assessment process.
For example, when using laptops at work, there can be a risk of them being stolen. Another risk associated with this can be that employees can use an insecure connection in public places, or someone can see the sensitive information on their laptop screen.
Evaluate the risks
At this stage, you should determine which risks need to be concerned about as some risks are more severe as compared to others. Risk criteria become very useful at this stage because it provides a guideline using which the company can compare the risks by assigning them a value according to the likelihood of their occurrence and the damage they can cause.
Related Template: ISO Management Template
By assessing the risks in this way, the organization can get a comparable as well as consistent analysis of the threats it can face. There is no set rule for gauging risks given by ISO 27001.
The organization can use any scale from high to low or 0 to 1 depending upon its needs, as long as all the people responsible for risk evaluation use the same scale.
Risk Assessment Template key Element
Different ways can be used for treating risks:
- Modification of the risk by using security controls to reduce the chances of occurrence of the risks of the damage caused by them.
- Avoiding the risks by altering the situations that are causing them.
- Retention of the risks by establishing that it falls under the criteria of previously accepted risks or by taking extraordinary decisions.
- Sharing risks with partners like an insurance firm or a third party that is well equipped to manage such risks.
Compile the Report of Risk Assessment
This is the step in which the risk assessment is document. This report is necessary for audit and certification. It consists of many reports but two major reports include:
SOA (Statement of Applicability)
This document contains a list of controls that can’t implement as well as an explanation about why they can or can’t select. The level of progress of implementation of the control is also stated in this document. It should also be explained why the controls that were omitted were consider irrelevant.
RTP (risk treatment plan)
A risk treatment plan provides a summary of every risk that was identified, responses designed to deal with the risk, causes of the risk, and the date for starting the risk treatment.
For more example or sample of Risk Assessment Template for ISO 27001, Contact PMPDOCUMENTS.COM

